The Best Guide To Internet Safety
Table of ContentsUnknown Facts About Internet SafetyVpn Services - QuestionsCybersecurity Training Can Be Fun For AnyoneThe smart Trick of Parental Control Software That Nobody is Talking AboutInternet Safety for DummiesSee This Report on Vpn Services3 Easy Facts About Vpn Services Described
This is essential because it permits companies to keep an affordable advantage and keep their services and products risk-free from rivals. In addition, it helps to ensure that new product or services are not easily reproduced or swiped prior to they can be launched to the market. The cloud has actually transformed exactly how we consider IT, however it has likewise presented new security dangers.
This dexterity can additionally present brand-new protection dangers. A cloud supplier may not have the very same security controls as a traditional on-premises information.
An Unbiased View of Internet Safety
They ought to deal with their cloud service providers to make certain that sufficient protection controls are in area. They need to also think about making use of a cloud protection platform to aid handle and monitor their cloud environment. The internet has come to be a staple in organization operations for most of business across the world.
By taking these steps, businesses can show their commitment to shielding client and also worker information, which can assist to build and maintain trust fund - Cybersecurity training. The value of cybersecurity to ensure a company's economic setting can not be understated. In today's interconnected world, where delicate information is commonly saved digitally, a violation in safety can have tragic repercussions
It is crucial to have this plan in position to make sure that organizations can promptly as well as properly reply to an attack. An additional essential facet of cybersecurity is staff member training. Staff members should be trained on how to find possible cyber threats as well as what to do if they come across one. This training can assist to lower the opportunities of a successful cyberattack.
Vpn Services - The Facts
There are many reasons why people need to secure their information. One reason is that if data is not covered, unauthorized people can access and also utilize it.
Another factor is that if information is not shielded, it can be lost or destroyed, which can create considerable inconvenience or also monetary challenge. Some ways people can progress at safeguarding their data are:: Passwords must be at the very least eight characters long and also include a mix of capital and lowercase letters, numbers, and also symbols.
And as we use it increasingly more, we are putting increasingly more of our personal details online. This information can be made use of to steal our identity, money, or information. One more factor to learn the value of cybersecurity is that cyber-attacks are coming to be much more as well as more typical, and also we need to be much more mindful than ever.
The Facts About Vpn Services Uncovered
A cyber-attack might disable a medical facility, bring down a power grid, or even begin a battle. Finally, it is crucial to discover cybersecurity since it is an expanding sector. There are an increasing number of task possibilities in cybersecurity, and also the area will only continue to grow. As we become much more reliant on modern technology, the requirement for individuals that can shield us from cyber-attacks will just enhance.
Organizations that need cybersecurity always deploy measures to ensure solid and also secure information retention. People likewise need to be watchful about their on-line task as well as take steps to protect their individual info. We can assist make the internet much safer for everyone with the right safety measures
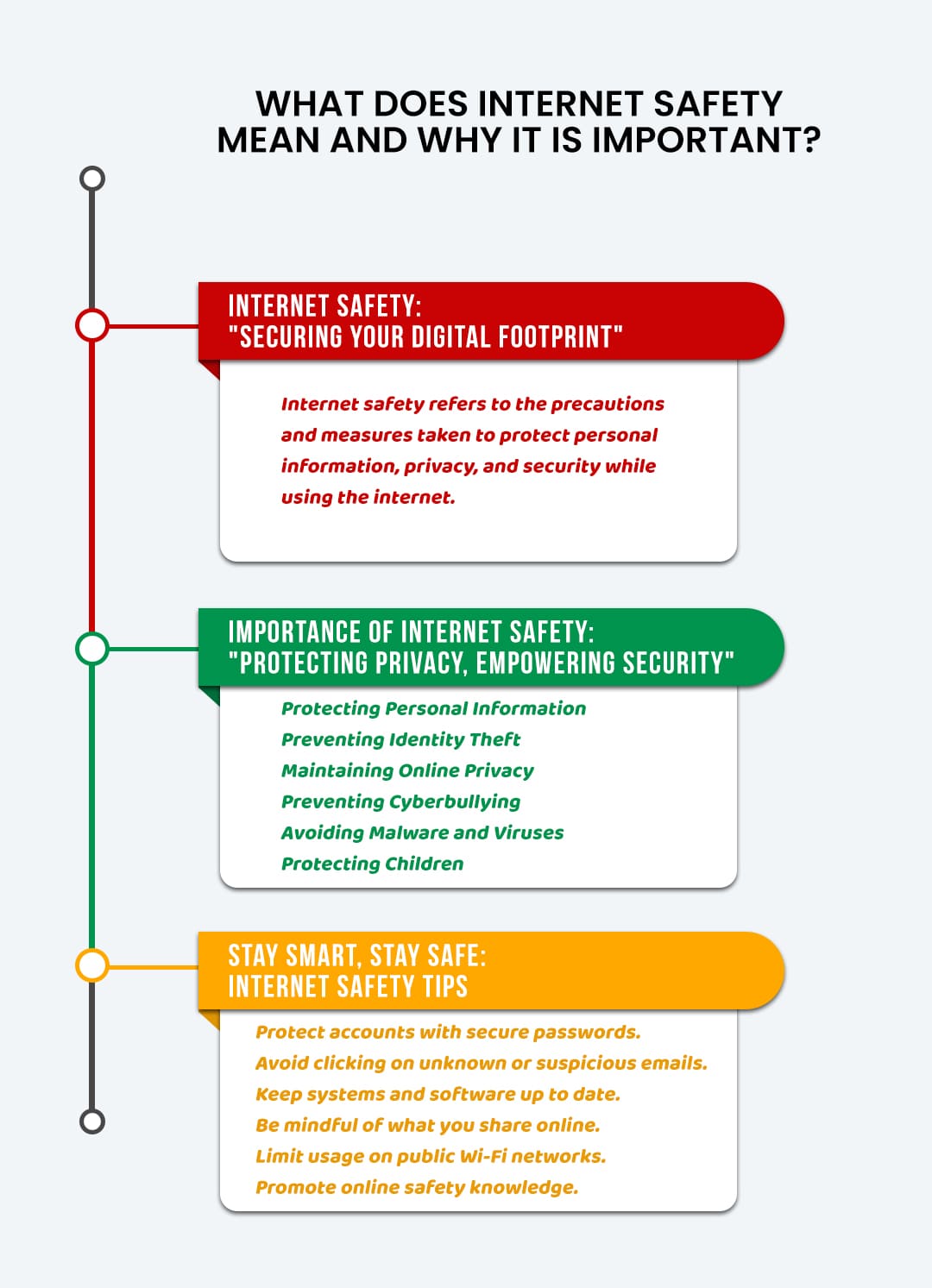
Being risk-free online suggests that you have the knowledge to determine the potential threats and also are conscious of your personal security while searching, sharing or surfing the net. By educating internet security, you are not only assisting your students end up being extra watchful regarding their own security, however additionally helping them progress users of the web.
How Vpn Services can Save You Time, Stress, and Money.
A lot of students nowadays have endless access to the net on their phones and also in the house, and it is very important that they are able to browse these online environments securely. Opening up a dialogue concerning risk-free techniques and dealing techniques with your students is a positive step towards establishing electronic literacy abilities.
Webwise has actually created a variety of lessons on the subject of on the internet safety and security, for both main and also post-primary level, you can find these in the source area of our website. These are fantastic to make use of in the classroom to elevate awareness as well as to establish great online methods with your pupils.
Along with this, trainees require to be conscious of their electronic footprint as well as their on the internet track record. Everything we post online adds to our digital impact and also what is placed online, frequently stays on the internet forever. You can utilize our vital assuming guide to assist your pupils examine their very own activities on-line and also come to be more mindful of how to use the internet responsibly.
The Definitive Guide to Cybersecurity Training
An effective online Safety Administration System or a safety and security as well as compliance administration software can make a substantial difference to your business. Using the most effective online security as well as conformity software program service has for that reason become crucial because it not only makes your job easier yet enables you and your company to concentrate on higher concern company tasks.


Cybersecurity Training for Beginners
As you can guess, hand-operated techniques are not only tedious however are susceptible to human errors. This is one aspect for which on-line security and compliance monitoring systems are created; to fix this issue - and considerably decrease reference errors. Despite how experienced and diligent your workers are, they are human beings who are most likely to make errors.
Having an on-line safety and security and conformity administration system is all regarding supplying a great experience for everybody involved. You should feel secure and also confident that your service is dedicated to safety and security and compliance, and also your workers should be committed every action of the means to attaining that. Therefore, on the internet tracking and reporting have actually become an important part of on-line security and also compliance monitoring systems.
Company success is as much about your effort as it is concerning the perception the general public has regarding your brand. By making use of an online safety as well as conformity administration tool, the general public identifies that you are taking security issues seriously as well as really feel the demand for everybody entailed in the service to be safe as well as confident in-and-around your work environment.